One-way encryption
When passwords are stored on a computer, it is essential that they be kept secret. Thus it is recommended practice to perform one-way encryption on a password before storing it on disk. One-way encryption involves scrambling the password via a hash function before storing it. When a user later enters their password, the entered password also gets "hashed" and then compared to the stored (hash-encrypted) string. It is not quite this simple, but that is the basic framework of what happens.
The password is usually encrypted as a hash digest (a large number generated by scrambling and condensing plain text letters). An example of a hash digest is SHA-1, which dates from 1994. The SHA-1 algorithm takes a string as input. The algorithm is a digest because the result is a fixed-size number. The SHA-1 algorithm always outputs a 160-bit number (20 bytes of storage). 48 decimal digits would be required to express this number, and it is usually displayed to humans as a 28-character, base-64 encoded string. Here are some examples:
Hello World z7R8yBtZz0+eqead7UEYzPvVFjw= VB L1SHP0uzuGbMUpT4z0zlAdEzfPE= vb eOcnhoZRmuoC/Ed5iRrW7IxlCDw= Vb e3PaiF6tMmhPGUfGg1nrfdV3I+I= vB gzt6my3YIrzJiTiucvqBTgM6LtM=
In the examples above, note that even very similar strings have quite different hash digests; the hash doesn’t tell us the length of source string, or its starting character, or anything else about it. SHA-1 is useful because it produces collision-free results. Below is C# (v2.0) code for producing an SHA-1 hash digest from a string:
Byte[] bytSource; // byte array for plain text string
Byte[] bytHash; // byte array for cipher string
System.Text.UnicodeEncoding uEncode = new System.Text.UnicodeEncoding();
System.Security.Cryptography.SHA1CryptoServiceProvider sha1 =
new System.Security.Cryptography.SHA1CryptoServiceProvider();
// fill byte array with Unicode chars from plain text source string
bytSource = uEncode.GetBytes(strSource);
// encrypt the source byte array into the result array
bytHash = sha1.ComputeHash(bytSource);
// return a displayable base64-encoded string
return Convert.ToBase64String(bytHash);
Hash digests are unique signatures and can be used to verify that a file has not changed. For example, the hash digest of an XML file can be sent (along with the XML file) to verify that the file wasn’t corrupted during transmission.
Use of one-way encryption for password storage and authentication
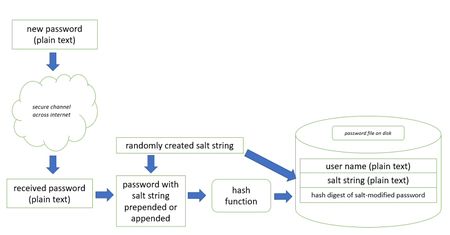
When implementing password security, it is best to use a tried and true software library which has already been developed and debugged, because the process of handling passwords is a little more complicated than merely creating a hash digest of a password. It turns out, that to minimize the likelihood of a dictionary attack on a password, it is necessary to salt the password by either prepending or appending a unique, randomly created string to it before it hashing and storage (new password) or hashing and comparison (existing password). There is a very good tutorial on salting passwords in the OAuth blog ("Adding Salt to Hashing: A Better Way to Store Passwords"[1]).
Use of one-way encryption for verification of file integrity
References
- ↑ OAuth blog: Adding Salt to Hashing: A Better Way to Store Passwords, last access 10/8/2020